User Tools
Table of Contents
Jboss encryption module and web frontend for TIM
TIM encoder uses a Jboss module for encryption and to validate keys. The encryption is used e.g. for database connections and third-party applications within the configuration files in order to hide sensitive information like usernames and passwords from plain sight.
To use this module the following steps need to be done:
- Add the encoder.war of the TIM Encryption Webarchive
- Modiy the standalone-tim.xml
- Generating a java key with web-interface or console
- Use encryption with TIM
Add the encoder.war of the TIM Encryption Webarchive
To enable TIM to encrypt usernames and passwords and to use those encrypted values insert the encoder.war to the standalone\deployments folder in your %JBOSS_HOME% e.g. C:\tim\jboss-eap-7.1\standalone\deployments. Upon JBoss startup it will deploy automatically.
Modify the standalone-tim.xml
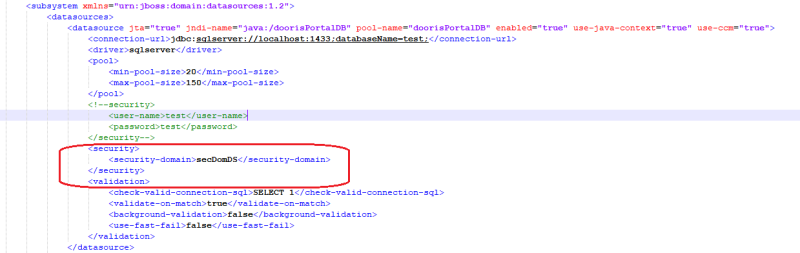 Changes in the standalone.xml are made accordingly. In your subsystem datasource below your database
implemet:
Changes in the standalone.xml are made accordingly. In your subsystem datasource below your database
implemet:
<security> <security-domain>secDomDS</security-domain> </security>
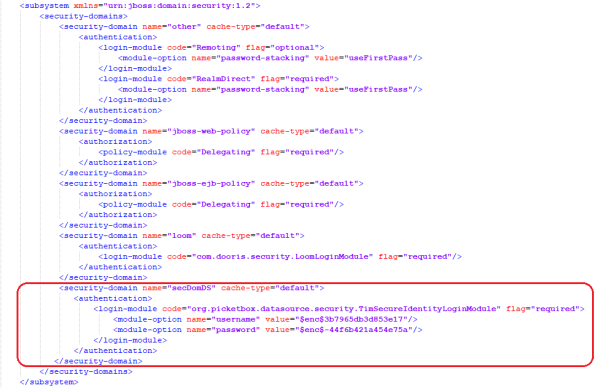
as can be seen in the first screenshot.
In the subsystem security add:
<security-domain name="secDomDS" cache-type="default"> <authentication> <login-module code="org.picketbox.datasource.security.TimSecureIdentityLoginModule" flag="required"> <module-option name="username" value="$enc$c5507593f47122e"/> <module-option name="password" value="$enc$-3c3702fd5f714bd0045dcdcdd12584c8"/> </login-module> </authentication> </security-domain>
Generating a java key with web-interface or console
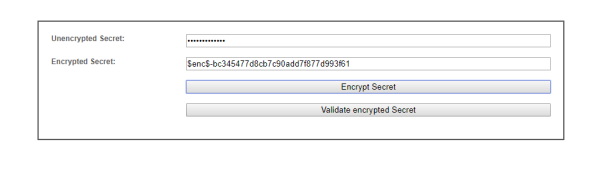
There are two ways to encrypt your credentials. Either with the web-interface or with via the console.
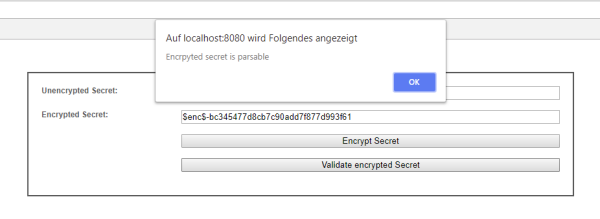
The module can be called via the web-interface e.g. http://your_tim_url:port/encoder/ . In oder to encrypt a secret insert use the text field and hit the encrypt secret button. To validate a encrypted secret past the secret in the correct text field and hit the validate encrypted secret button. This method can as well be used to encrypt any secret in e.g tim.properties.
To encode your credentials via console use the following commands:
to generate a key:
java -cp modules/system/layers/base/org/picketbox/main/tim-encoder-module.jar:modules/system/layers/base/org/picketbox/main/picketbox-4.1.1.Final-redhat-1.jar org.picketbox.datasource.security.TimSecureIdentityLoginModule '123'
to validate password-key combination:
java -cp modules/system/layers/base/org/picketbox/main/tim-encoder-module.jar:modules/system/layers/base/org/picketbox/main/picketbox-4.1.1.Final-redhat-1.jar org.picketbox.datasource.security.TimSecureIdentityLoginModule '123' '$enc$b530c41fe274111'
to validate the key:
java -cp modules/system/layers/base/org/picketbox/main/tim-encoder-module.jar:modules/system/layers/base/org/picketbox/main/picketbox-4.1.1.Final-redhat-1.jar org.picketbox.datasource.security.TimSecureIdentityLoginModule '' '$enc$b530c41fe274111'
TIM Properties
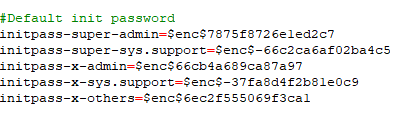
In tim.properties credentials can be encrpyted with the encoder or the console and replace plain text usernames and passwords. As an example the image shows setting and editing the superuser and client-administrator passwords:
E-Mail Configuration
In the properties of the client unter the category mail server are the paramters SmtpUser and SmtpPassword.
These credentials can be encrypted accordingly to the methods above and as shown in the example. 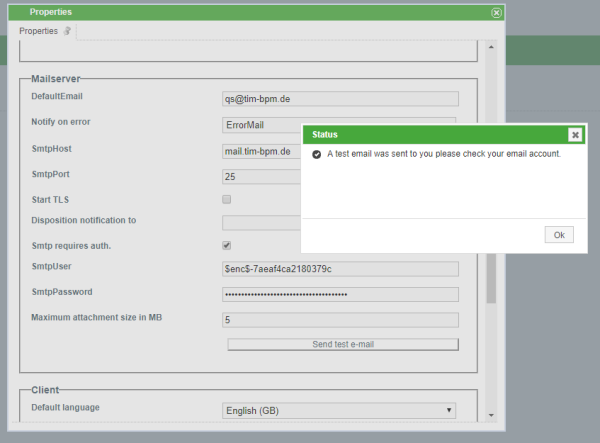
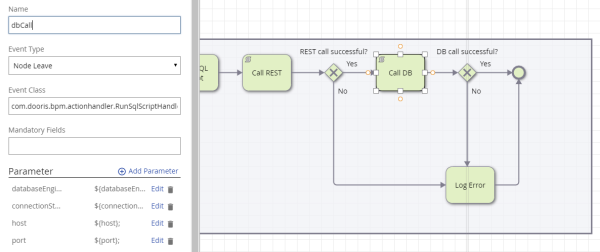
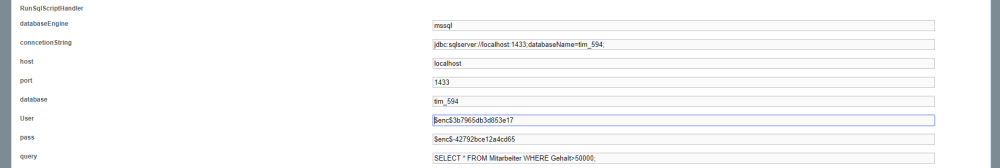
Actionhandler
Actionhandler like HTTPRequestHandler or RunSqlScriptHandler use credentials that can be encrypted by said methods. The example shows the RunSqlScriptHandler where ${user} and ${pass} are passed on encrypted via smartform: